“Your protection starts with a firewall. Let’s ensure your protection is set !”
There are hackers spreading malicious data to your networks and a firewall acts as a barrier to prevent the entry of malicious data into the network by blocking unknown traffic from entering your network and thereby securing the network from cyber attacks. Firewall plays a vital role and it is an essential layer of security in protecting your personal/companies data and will safeguard your network/servers from various attack vectors.
What is a Firewall?
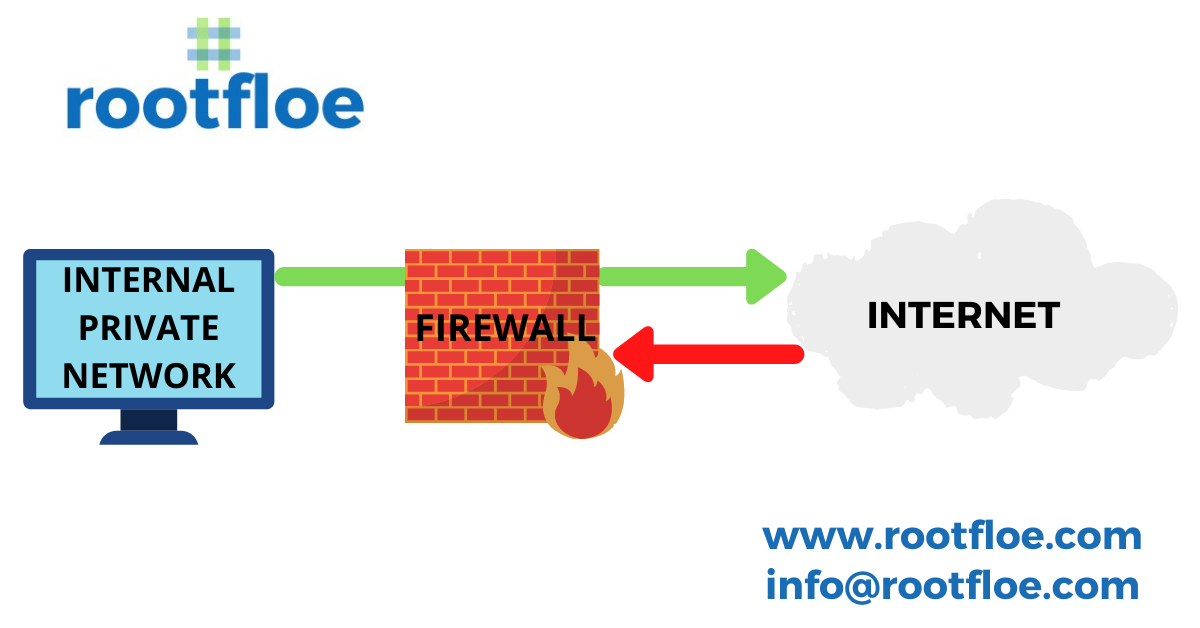
A firewall is the first line of security integrated (i.e.,Through hardware/software) to your network and monitors the incoming and outgoing traffic and also blocks unwanted suspicious traffic. A firewall consists of predefined security regulations on blocking and identifying suspicious traffic and thereby enabling smooth progression on authorized packets. Firewall not only blocks unwanted data but also protects a site from malicious data and has the capacity to keep the threat at bay.
How does a Firewall work?
Firewall not only filters the incoming traffic but also monitors the outgoing traffic as well. The outgoing traffic from our server is monitored to check if the packets are not sent to any suspicious targets. There are different types of firewalls and it is important to implement the appropriate one according to the needs.
Types of Firewalls :
- Packet Filtering Firewall
- Stateful Inspection Firewall
- Next-Generation Firewall (NGFW)
- Application Level Gateway or Proxy Firewall
- Circuit Level Gateway
1. PACKET FILTERING FIREWALL :
Packet filtering firewall is the oldest of firewalls which filters and examines every packet that passes through it. It does not examine the data inside the packets. It allows the packets if the information in the headers satisfies the rules and this firewall is comparatively faster. It inspects some base level information such as source address, a destination address, port number, etc.
Some packet filters aren’t able to recognize the packets that are blocked before. But, most of the packet filters recognize the used packet filters by its port address, IP address, and other credentials.
2. STATEFUL INSPECTION FIREWALL :
Stateful Inspection Firewall keeps track of incoming traffic and allows or blocks those traffic by checking its state, port, and protocol. This firewall works on both user-defined or context rules. This firewall has the ability to identify active connections. It is easy to bypass a stateless firewall, but a stateful firewall provides more control over blocking or allowing a specific packet. It is very complex to set up stateful firewalls and requires more computer resources as it keeps track of active connections.
3. NEXT-GENERATION FIREWALL (NGFW) :
Next-Generation Firewall is very secure when compared to the traditional firewalls. This firewall performs all the processes that a stateful firewall and can also deeply inspect the traffic and perform actions such as intrusion prevention, website filtering, application control, malware detection.
NGFW understands the nature of the data transfer, providing multi-layer protection by analyzing the packets. The NGFW doesn’t need to have a separate setup to configure, it can be accessed from a single console.
4. PROXY FIREWALL OR APPLICATION LEVEL GATEWAY(ALG):
Proxy firewall filters the incoming traffic at the application level, where the communication between the client and the server is configured through a proxy. Whenever a user tries to connect to a host, the connection is first directed to a proxy server inspecting the incoming traffic and then let the user is connected to a host. Application-level gateway (ALG) needs the proxy to support services such as SMTP, HTTP, FTP, etc. In an ALG only the firewall is visible to the users independent of what service they acquire, this helps to protect the internal data of the server. However, to make sure that the incoming packets are free from malware, a Proxy firewall is able to perform a deep layer packet inspection and due to the procedures, it follows it is slightly slower.
5. CIRCUIT LEVEL GATEWAY:
Circuit level gateways are not most effective as they only inspect the TCP handshake and don’t check the packet’s data. Circuit Level Gateway works by verifying TCP Handshake, the packet is allowed once the request session by a handshake is legit. Even a packet with a legit TCP handshake containing suspicious data is allowed by the Firewall. It doesn’t consume a lot of the computer’s resources as it only verifies the TCP handshake and doesn’t inspect the internal data.
As firewalls act as the entry-level protection for any computer network or website, windows and mac operating systems have in-built firewalls to prevent the entry of malicious data.
When it comes to the enterprise level, both external and internal firewalls are used. An external firewall gives protection to the applications in the demilitarized zone (DMZ). Internal firewalls do high-level filtering of packets giving more protection to the internal systems like databases, workstations, etc. There are a wide range of firewalls available and every type has its own pros and cons which is why it is advisable to implement the most suitable one according to the business requirements.
Get in touch with us today for a free consultation about our Firewall Security Services at info@rootfloe.com.