Microsoft has released today its monthly batch of security updates, known as Patch Tuesday. This month, the OS maker has fixed 56 security vulnerabilities, including a Windows bug that was being exploited in the wild before today’s patches.
Category: Compliance
FireEye Cyber breach – PART II
No organization is 100% secure – ever! As FireEye continued to investigate and identify the root cause of their security incident, they identified a global campaign that introduced a compromise into the networks of public and private organisations through the software supply chain. FireEye identified that this compromise was delivered through a widely used IT infrastructure management and remote monitoring software – SolarWinds. Although FireEye hasn’t attributed this attack to any particular group, based on several media reports, it is believed that this attack was carried out by a nation-state…
Fireeye Cyber Breach – PART I
No organization is 100% secure – ever! FireEye is one of the world’s renowned cybersecurity firms with customers including major government agencies and enterprise customers around the world. The company is known for its world-class research on state-sponsored threat actors and its incident response capabilities. On 8th December 2020, FireEye CEO Kevin Mandia said in a public statement that they were recently attacked by a highly sophisticated threat actor. “This attack is different from the tens of thousands of incidents we have responded to throughout the years. The attackers tailored…
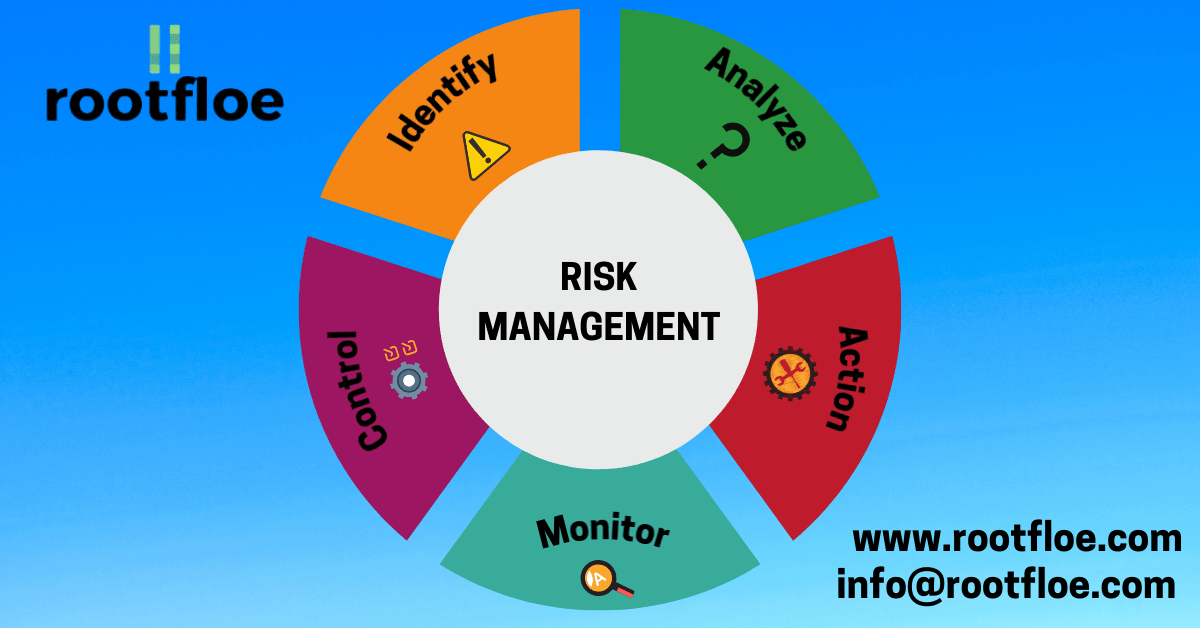
Risk Management
“Be Prepared for Anything!” What is Risk Management? Risk Management can be defined as the process of identifying, evaluation and prioritization of risks and further plan to monitor and reduce the impact of unfortunate incidents. ISO 31000 classifies risk management process into the following steps; communication and consultation; establishing the context; risk assessment, risk identification; risk analysis; risk evaluation; risk treatment; monitoring and review. Risk Management is an iterative process. Why is it important? Risk can come from different sources in and out of an organization. It is important to…
Identity and Access Management
Data is the most important thing when it comes to cybersecurity. To protect one’s data, we should be aware of who has access to the data, only the authorized person with defined permissions should be able to access the data. IAM verifies and manages different permissions for different employees according to their role in the organization.
Information Security Management Systems
A company is only as strong as the rules it’s built on.
“An art of exploiting Human Psychology”-Social Engineering
“An art of exploiting Human Psychology” Nowadays it has become harder to fight against the social engineering attacks than the technical attacks because the social engineering attack has the capability to bypass all technologies including the firewalls. What is Social Engineering? Social engineering is a technique used by attackers to persuade people into performing actions and revealing private information that may be useful for fraudulent purposes. In today’s world humans are more susceptible to attacks by the bad guys than machines. So it is very important for an organization to…
GDPR & Related Fines to grow by the year 2025 to encourage more companies to follow the law
”Fines to grow by the year 2025 to encourage more companies to follow the law” The legislation for data protection was much in shambles causing chaos and confusion to organizations, business and individuals all alike. Post GDPR introduction the privacy law to protect all has been declared the toughest data protection law in the world. What is GDPR?General Data Protection Regulation (GDPR) is a mandatory legal framework which provides and sets guidelines for the collection and processing of personal information from individuals who live in the UK and the European…